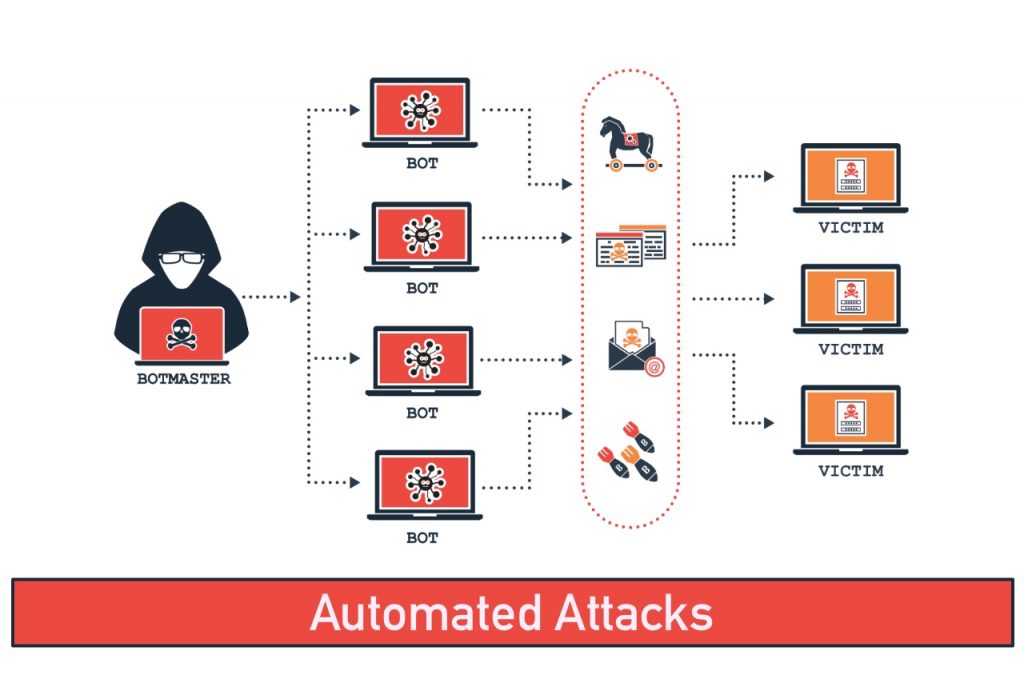
Bad bots carry out a range of applications such as content and price-scraping. They scrape proprietary data from websites and online services, package this data, and sell it to companies who wish to buy it to use as a competitive tool. Website security should be our priority. Another huge market for bad bots is so-called credential stuffing attacks. Credential stuffing cyberattacks involve the use of credentials gained from a data breach being used to try and log into other services in which the rightful owner of those credentials may have an account. While many users will do the correct thing of having different login details such as usernames and passwords for every service they use, that is not always the case. A fraction of users will reuse the same login details for ease of use. There is, of course, no guarantee that users will have accounts at particular targeted services (for example, John Smith having the username “John.Smith84,” the password “Johnspetdog” and an account at the American National Bank). However, if even a tiny number of users yield positive responses, that could still be a high enough success ratio for hackers to consider it a worthwhile endeavor.
Bad bots, bad bots, whatcha gonna do?
Lots of estimates peg the rate of success for credential stuffing attacks at 0.1%. This means that there is likely to be at least one successful hack for every thousand accounts that are tried. But although that would be frustratingly low odds if the credentials had to be entered manually by hackers every time, advanced bot tools mean that credential stuffing attacks can be carried out through automated means. It’s simply a matter of allowing bots to run through different combinations at high speed. Bot-driven credential stuffing attacks can be extremely large and prolonged. For instance, it is easily in the realms of possibility (and even commonplace) to have an attack that lasts for several days and includes tens of millions of login attempts. These attacks can be damaging to individual customers (who wants a bot having access to their banking details?), as well as to companies. These companies will have to deal with the criminal aspect of fraudulent requests and, potentially, having their services slowed down or even brought to a halt by massive credential stuffing attacks. While the goal may differ from a volumetric DDoS (distributed denial of service) attack, large scale credential stuffing attacks nonetheless throw massive numbers of requests at websites and online services. In many cases, their servers may not be equipped to handle it.
The issue is becoming more widespread.
Several factors have made such bot attacks more commonplace. One is the increased frequency of massive data breaches. For example, earlier in 2020, an enormous hack of the Marriott International hotel chain resulted in 5.2 million records stolen. This is by no means the largest such hack. In October 2013, hackers stole data amounting to 153 million user records consisting of customer names, user IDs, passwords, debit and credit card details. This data frequently finds its way into the hands of other bad actors who may use it to orchestrate attacks such as credential stuffing cyberattacks. A report from 2020 notes that a hacker group named ShinyHunters put 91 million user records — supposedly gathered from 10 hacked companies — up for sale for just $5,000. That’s a tiny percentage of a penny per user. There are reportedly 15 billion user credentials currently for sale in hacker forums online. As more and more of our lives and activities take place online, not only does the quantity of data, it is possible to steal increase, but so does the potentially damaging scope of such attacks. The big challenge from a detection point of view is that it’s harder than ever to identify bot behavior — and therefore, to keep out the bad actors. The more sophisticated bots can replicate the mouse movement and clicks that systems use to spot automated bots. But even simple bots can be difficult to spot on the first try. It is hard to differentiate a legitimate attempted login from an attacker carrying out a credential stuffing attack on the first attempt. Therefore, companies are stuck between being unable to act, resulting in increased fraud, or recognizing too many false positives, and locking legitimate customers out of their accounts while raising massive numbers of customer service tickets for employees to have to deal with.
The importance of proper protection
In short, bots waste resources and place user accounts at risk. Companies need to protect themselves against these attacks, which can prove extremely costly and damaging to customer loyalty. There are measures that companies can put in place, such as monitoring traffic sources for issues like high bounce rates and lower-than-expected traffic conversion rates from certain unexplained spikes. However, the best option is to hire experts with a suitable history of bot detection who can help. Tools like proper Web Application Firewalls, otherwise known as a WAF, can be a gamechanger. The biggest problem with bot attacks is how unrelenting they can be. It truly is a 24/7 problem that companies face. That’s why you must select an equally 24/7 dedicated team of experts to help protect you against the problem.